THE BAD NEWS
From heartbleed.com
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
LA TIMES article says:
“Avoid things like online banking and avoid sensitive sites if you’re not sure,” said Andrew Storms, director of DevOps at CloudPassage. “Some people will see it as overkill. But I think that’s the simplest guidance. If you can hold off doing something online for a couple days, then you should.” http://www.latimes.com/business/la-fi-web-vulnerability-20140409,0,3935723.story#ixzz2yNFIPszd
NY Times article says:
“The most immediate advice from security experts to consumers was to wait or at least be cautious before changing passwords. Changing a password on a site that hasn’t been fixed could simply hand the new password over to hackers.” http://tinyurl.com/l3hh9j6
Art Zemon of Hens Teeth Network says: “Breathe and wait a few days before embarking on such a labor-intensive course as changing passwords everywhere.”
This is such a major problem that I would expect most servers to be updated within a week.
THE GOOD NEWS
The GOOD NEWS is that you’re probably OK if you and the server are using older software (prior to Dec 2011). All (or most) Macs & Mac servers have good versions of OpenSSL. To be clear, Macs & Mac servers don’t seem to be in any danger of being attacked directly. However, the danger of a server being attacked and leaking data is still there. To see if the server you want to use is vulnerable or not, see below “How to test other servers”.
From heartbleed.com:
What versions of the OpenSSL are affected?
Status of different versions:
• OpenSSL 1.0.1 through 1.0.1f (inclusive) are vulnerable (BAD)
• OpenSSL 1.0.1g is NOT vulnerable (OK)
• OpenSSL 1.0.0 branch is NOT vulnerable (OK)
• OpenSSL 0.9.8 branch is NOT vulnerable (OK)
Bug was introduced to OpenSSL in December 2011 and has been out in the wild since OpenSSL release 1.0.1 on 14th of March 2012.
OpenSSL 1.0.1g released on 7th of April 2014 fixes the bug.
HOW TO TELL WHAT VERSION OF OPENSSL YOUR MAC HAS:
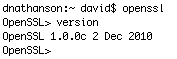
Open “Terminal” app (from /Applications/Utilities)
and type: openssl
Then when it comes back with: OpenSSL>
you type: version
and it will tell you what version of OpenSSL it is using. Compare that version to the list above of good & bad versions.
You may now “Quit” the Terminal app. We are finished with it.
Some Examples:
Mac OSX 10.9 Mavericks
OpenSSL 0.9.8y 5 Feb 2013 <– OK
Mac OSX 10.8.5 Mountain Lion
OpenSSL 1.0.0c 2 Dec 2010 <– OK
Mac OSX 10.7.5 Lion
OpenSSL 0.9.8r 8 Feb 2011 <– OK
Mac OSX 10.6.8 Snow Leopard:
OpenSSL 0.9.8x 10 May 2012 <– OK
Mac OSX 10.5.8 Leopard
OpenSSL 0.9.7l 28 Sep 2006 <– OK
from Mac OSX 10.4.11 Tiger
OpenSSL 0.9.7l 28 Sep 2006 <– OK
Mac OSX 10.3.9 Panther
OpenSSL 0.9.7l 28 Sep 2006 <– OK
Another victory for Mac! :-)
This website is hosted at Dreamhost running Linux:
Welcome to fuchsia.dreamhost.com
[fuchsia]$ cat /proc/version
Linux version 3.2.45-grsec-2.9.1-r3+ (root@cerebrum) (gcc version 4.6.3 (Gentoo Hardened 4.6.3 p1.13, pie-0.5.2) ) #63 SMP Fri May 24 02:11:07 UTC 2013
[fuchsia]$ openssl
OpenSSL> version
OpenSSL 0.9.8o 01 Jun 2010 <– OK
WHAT DO WE DO ABOUT IT?
* If you have a bad version of SSL on your machine, fix that first. (Mac users- you guys are OK, no worries here). ![]()
* Test important servers before you login to them. See How to Test Servers” below.
* You’re going to need to change your passwords for some servers. But not yet! Wait for a few days maybe a week, until those servers are fixed. Then change your passwords there.
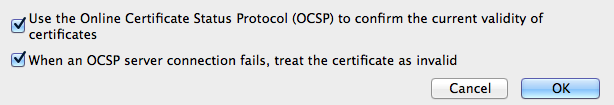
* Set your web browser to notice revoked SSL certificates. (below)
* Log Out of a website when you are finished with it. Don’t just close the window. Log out. There is always a menu or button or something to let you Sign out. Look for it. When you log out, most servers will discard your data from ram memory, so it can’t be retrieved by the Heartbleed bug.
Keep track of all those annoying passwords & related bits of important info. I like 1Password and I use it about a hundred times a day.
Certificate Revocation
Even if your computer has a good version of OpenSSL, the server you want to connect to may be vulnerable. A related problem is that many web browsers ship with default settings that do not even check for revoked certificates. Tsk tsk. These are settings we can fix.
![]() Safari users: You may be surprised to find that these settings are not actually in Safari, but in a separate app you’ve probably never used.
Safari users: You may be surprised to find that these settings are not actually in Safari, but in a separate app you’ve probably never used.
Open KeyChain Access. You’ll find it in the /Applications/Utilities folder
Pull down the menu to Preferences.
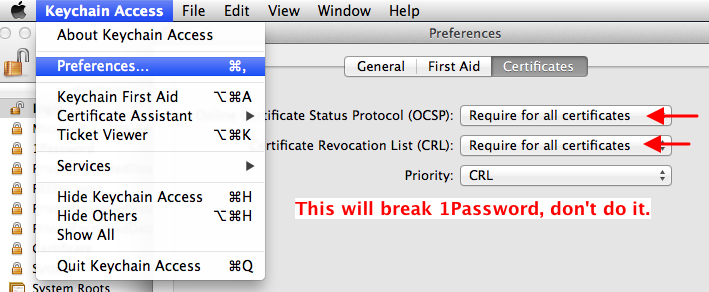
Click the “Certificates” tab, Then hold down the Option key, choose “Require for all certificates” for both of the first 2 items. Leave the 3rd one as it is.
Update: Don’t do that – it breaks 1Password & will prevent 1Password from launching. It also breaks Parallels.
But it seems OK to select “Require if certificate indicates”. Reboot for this setting to take effect.
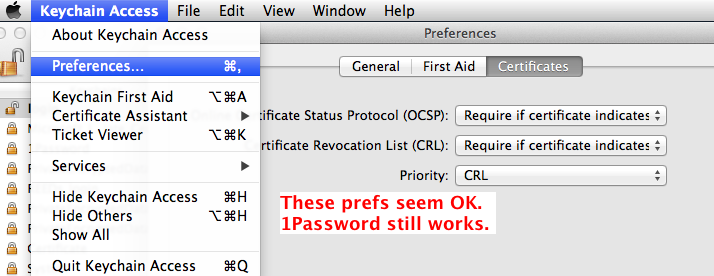
Ok! That’s better! Close the window & Quit Keychain Access. We’re done here.
![]()
HOW TO TEST SERVERS (before you login to them):
To test out how good the security is at your bank, webmail, or other SSL secured website, try this website tester. ssllabs.com/ssltest/
or this more basic one: filippo.io/Heartbleed/
WANT TO KNOW MORE?
Duncan Davidson, an engineer for German software company Wunderlist has written a personal account of what happened in more technical detail.
Bruce Schneier, who does not have a track record for being an alarmist, has declared the Heartbleed bug “catastrophic … On the scale of 1 to 10, this is an 11.”
As usual, XKCD nails the issue in beautiful form. (Image usage terms)
